According to a new study from Protiviti, engagement by a company’s board of directors is a critical factor in best managing information security risks.
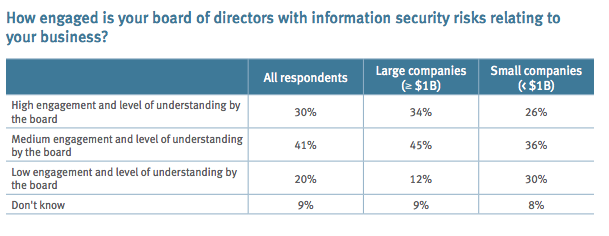
Overall, engagement and understanding of IT risks at the board level has increased, yet one in five boards still have a low level of comprehension. As the report states, this suggests “their organizations are not doing enough to manage these critical risks or engage the board of directors in a regular and meaningful way.” Further, while large companies do exhibit stronger board-level engagement, it is not a dramatic distinction.
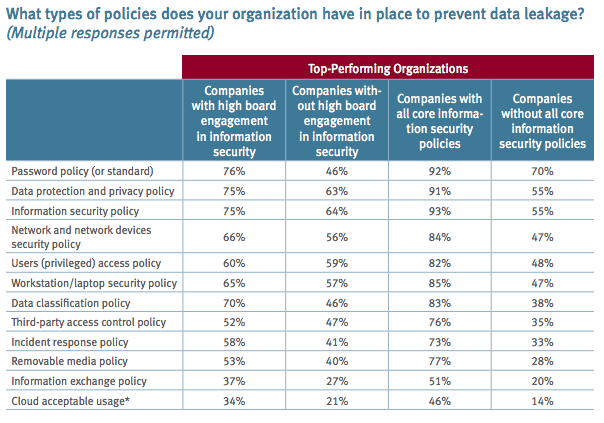
Of those companies that have implemented all core security policies—an acceptable use policy, record retention and destruction policy, written information security policy (WISP), data encryption policy, and social media policy—78% have boards with a high or medium level of engagement on information security. Even rudimentary security measures appear to vary with board engagement. Three out of four organizations with engaged boards have a password policy, while just 46% of those with medium or low levels of engagement have this basic provision in place.
The study did find two particularly alarming trends, both in companies with and without risk-aware boards. There was a significant increase this year in the number of organizations without a formal, documented crisis response plan to address data breach or cyberattack. Further, a surprising number of companies still do not have core information security policies. “One in three companies do not have a written information security policy (WISP). More than 40% lack a data encryption policy. One in four do not have acceptable use or record retention/destruction policies. These are critical gaps in data governance and management, and ones that carry considerable legal implications,” the report states. “On the other hand, organizations with all of these key data policies in place have far more robust IT security environments and capabilities.”
Similar Posts:
- Eliminating Language Barriers Between Information Security and the C-Suite
- Information Security Teams Drastically Underfunded, Understaffed
- Boards Are Failing at Cyber, New Report Finds
- Risk Management, Board Collaboration Can Bolster Cyber Defense
- 5 Questions Boards and the C-Suite Should Be Asking About Cyberrisk