
Since its launch in August, Samsung’s rollout and subsequent recalls of the Note 7 have been severely affected by quality and safety issues as a result of the lithium-ion batteries overheating, and in some reported incidents, even catching fire. This ultimately led to an initial recall on Sept. 15, followed by many incidents of phones continuing to catch fire even with the battery “repair,” and mobile carriers halting sales of the phone.
On Oct. 11, Samsung permanently halted all production and sales of this device. Current estimates from the Wall Street Journal indicate that “investors have shaved off roughly $20 billion in Samsung’s market value, [and] the company has said the recall would cost it $5 billion or more, including lost sales.”
To make matters worse, the Department of Transportation (DOT) has now weighed in and banned passengers from traveling with the phones. The DOT has issued an emergency order to ban all Samsung Galaxy Note 7 smartphone devices from air transportation in the United States. Individuals who own or possess a Samsung Galaxy Note 7 device may not transport the device on their person, in carry-on baggage, or in checked baggage on flights to, from, or within the United States. The Samsung Galaxy Note 7 device is now considered a forbidden hazardous material under the Federal Hazardous Material Regulations.
The initial recall would be expected to directly affect sales levels of the specific phone, and it would be fair to anticipate the possibility of a financial impact from a recall. But the further problems go beyond that—they lead to broader reputational issues.
Although all recalls will likely result in some financial impact and market frustrations, an isolated event can be a well-managed, short-lived issue, with a reasonably prompt recovery. Many customers may look past a one-off instance as a bump in the road, which has been identified and corrected—an error. A second or third problem arising after addressing the initial issue(s), however, and the company’s overall quality assurance programs are put in the spotlight. Customers are now looking beyond the isolated incident and lose confidence in the brand as a whole.
The extent of the financial losses resulting from this can grow exponentially as the result of a second or third similar issue.
The suggestion now develops that the company cannot determine what’s wrong or find a solution.
It appears that happened with Samsung, leading to the announcement that they are ceasing production of the model completely. Consumer confidence takes a big hit.
This year, we have seen the impact multiple recalls have had on several companies. Samsung, along with others like Chipotle, Takata Airbags and Mattel, have suffered repeat issues stemming from an initial problem. Where a company repeatedly has quality assurance issues, direct and manageable losses can quickly grow to larger exponential ones fueled by the broader reputational harm. Appearing in the media for the first problem had a significant financial impact. Reappearing after the initial handling of the matter is a less than ideal way to restore confidence and set about moving on from the issue.
The losses Samsung will suffer now extend beyond the costs to investigate the problem, recall logistics, and rework costs. They now face the more complicated challenge of measuring the business income lost from the event. An initial recall, and the replacement of phones would have likely led to some business income loss. While this may not have been avoidable, it would likely have been manageable. Not being able to identify the problem and develop a solution, however, has led to larger reputational issues and a much larger business income impact.

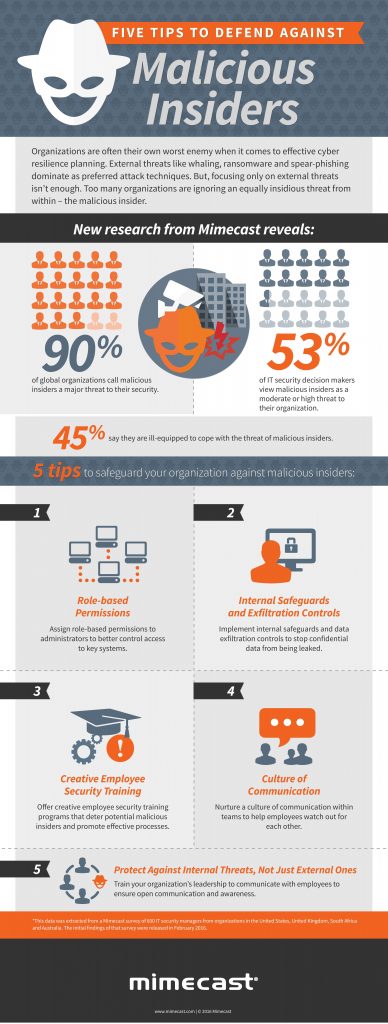

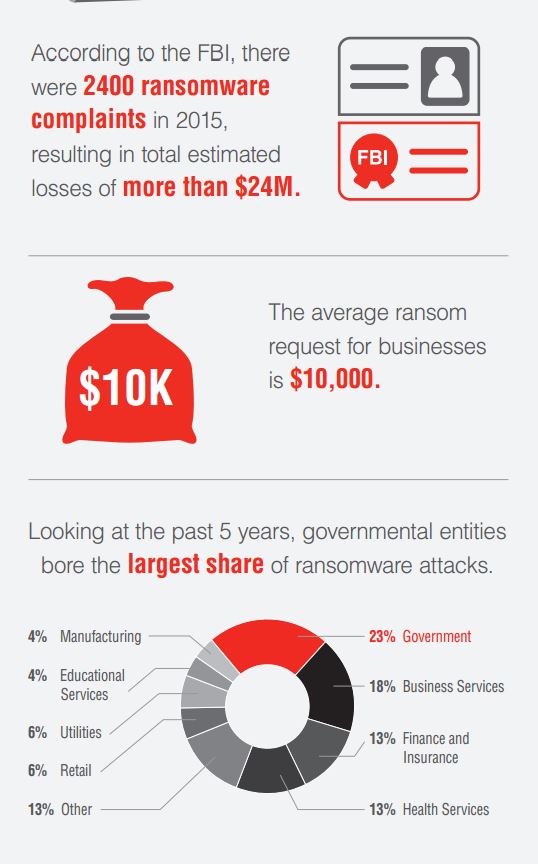
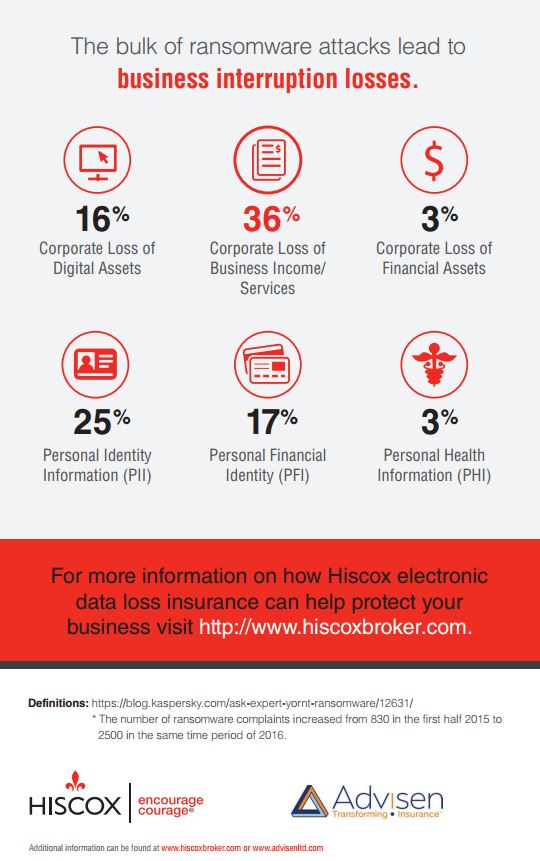
 Today’s headlines are full of reports of ransomware, retail customer data breaches and routine government surveillance of online traffic. The battle between the FBI and Apple over unlocking an iPhone is just the latest story highlighting digital data security as a daily concern.
Today’s headlines are full of reports of ransomware, retail customer data breaches and routine government surveillance of online traffic. The battle between the FBI and Apple over unlocking an iPhone is just the latest story highlighting digital data security as a daily concern.